Please scroll down to explore examples of how X•Protected can be deployed.
Below, you’ll find demonstrations of the system automatically recognizing and identifying hidden potential threats.
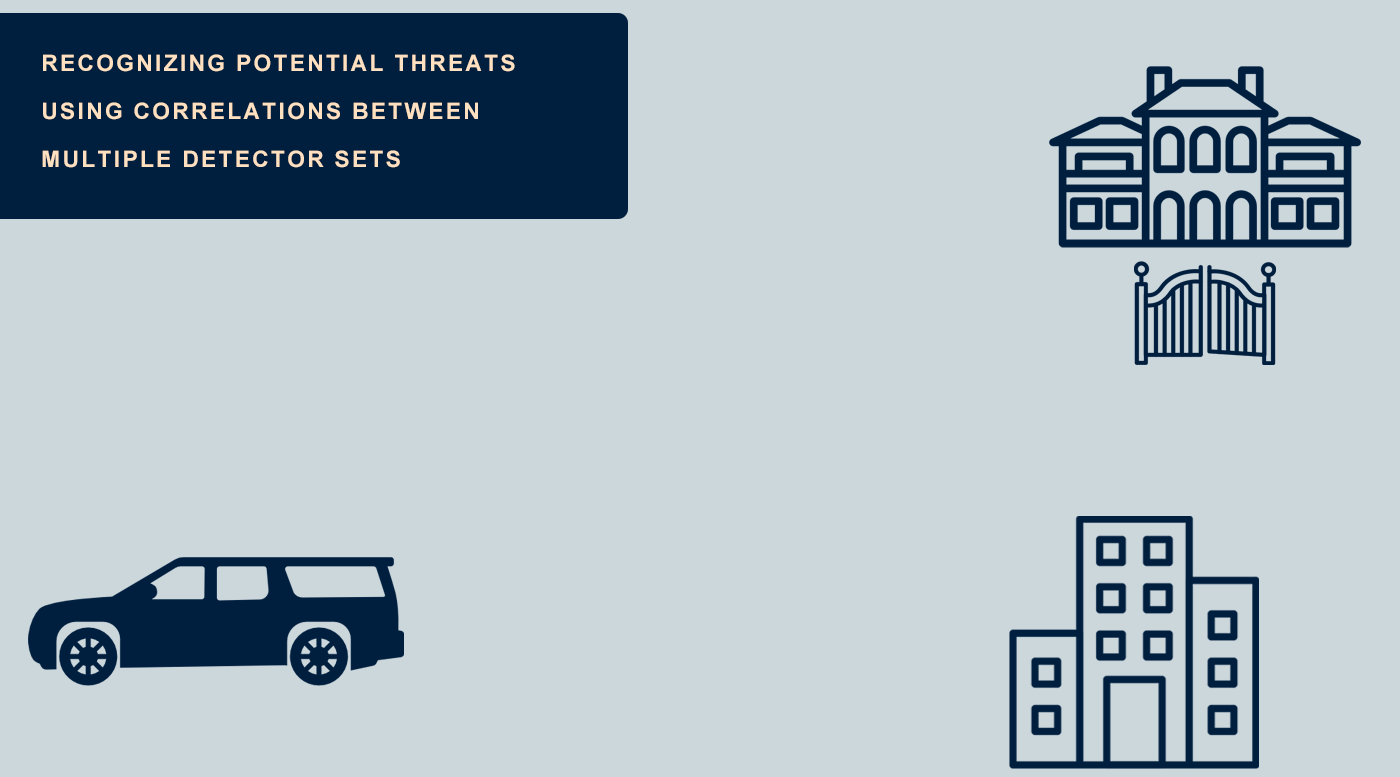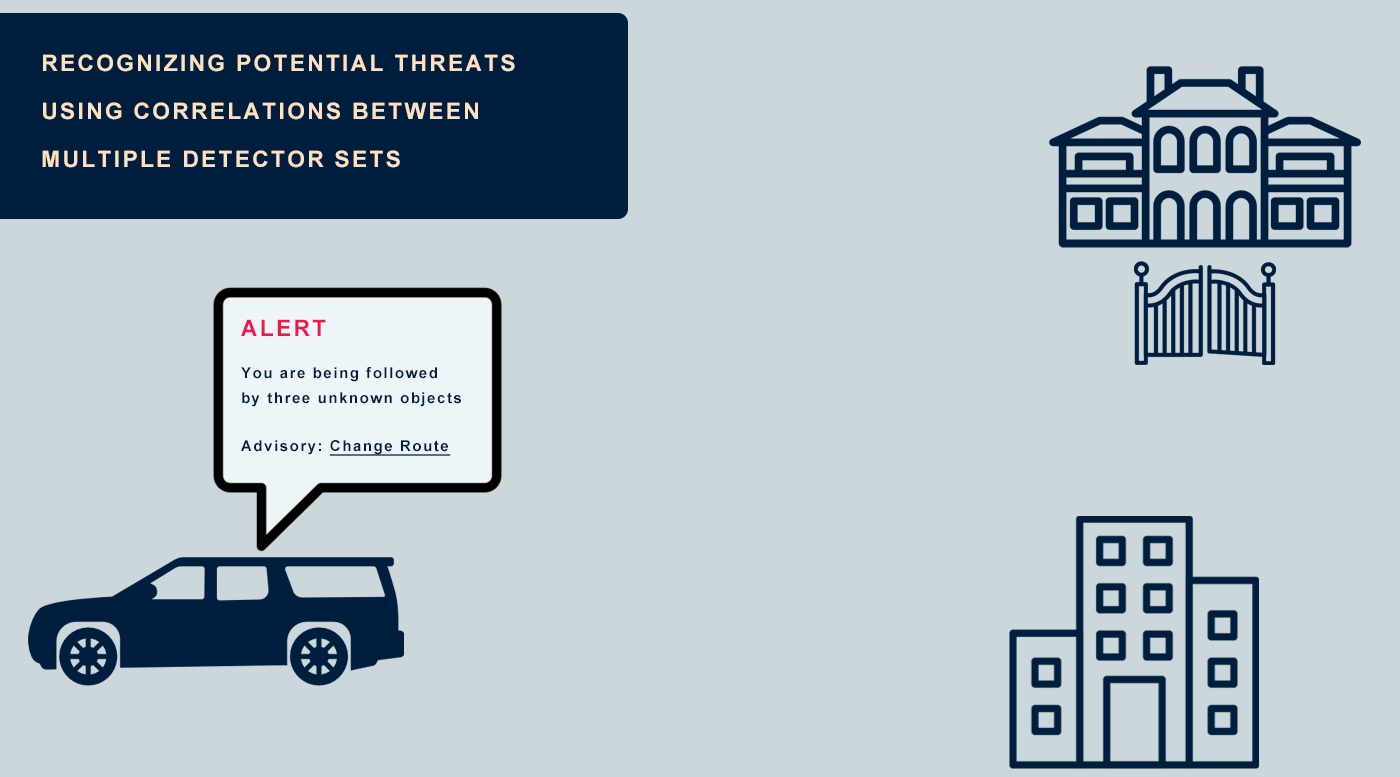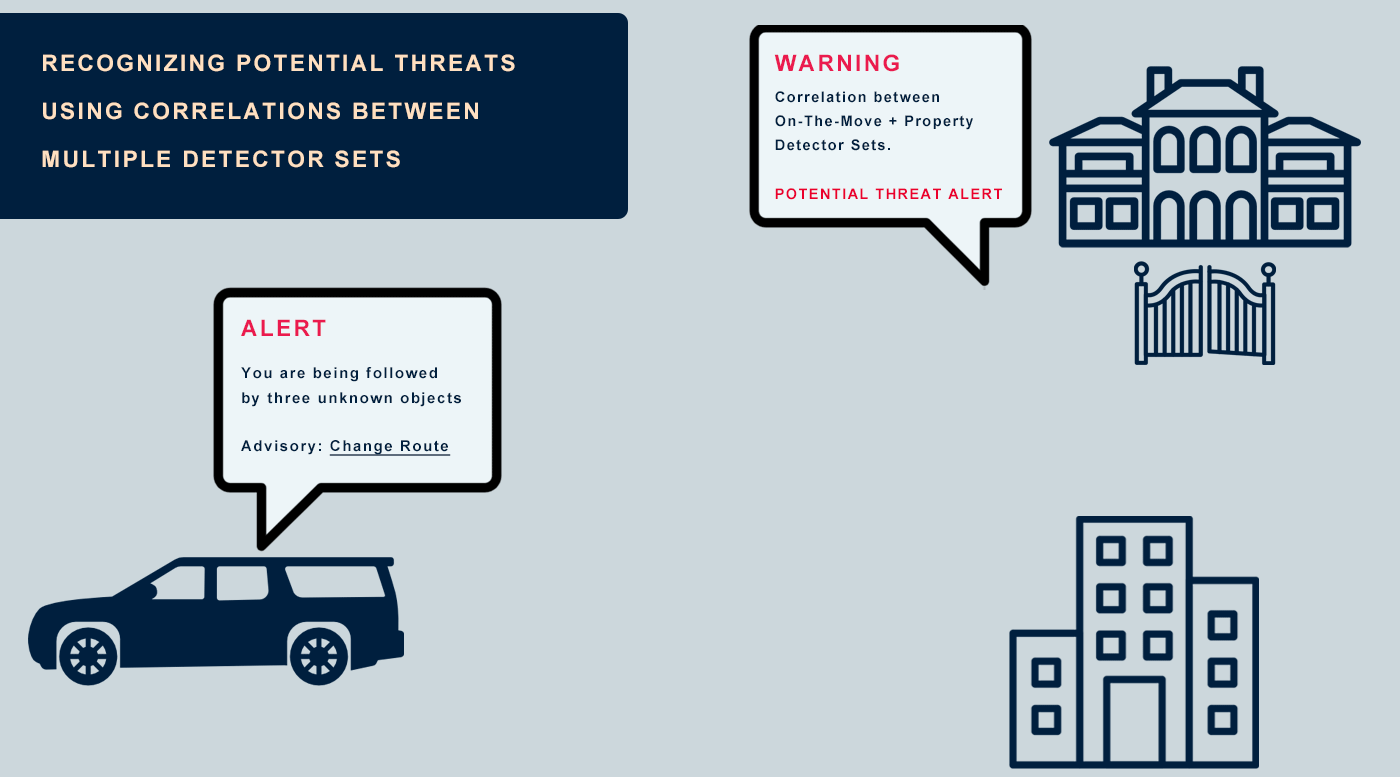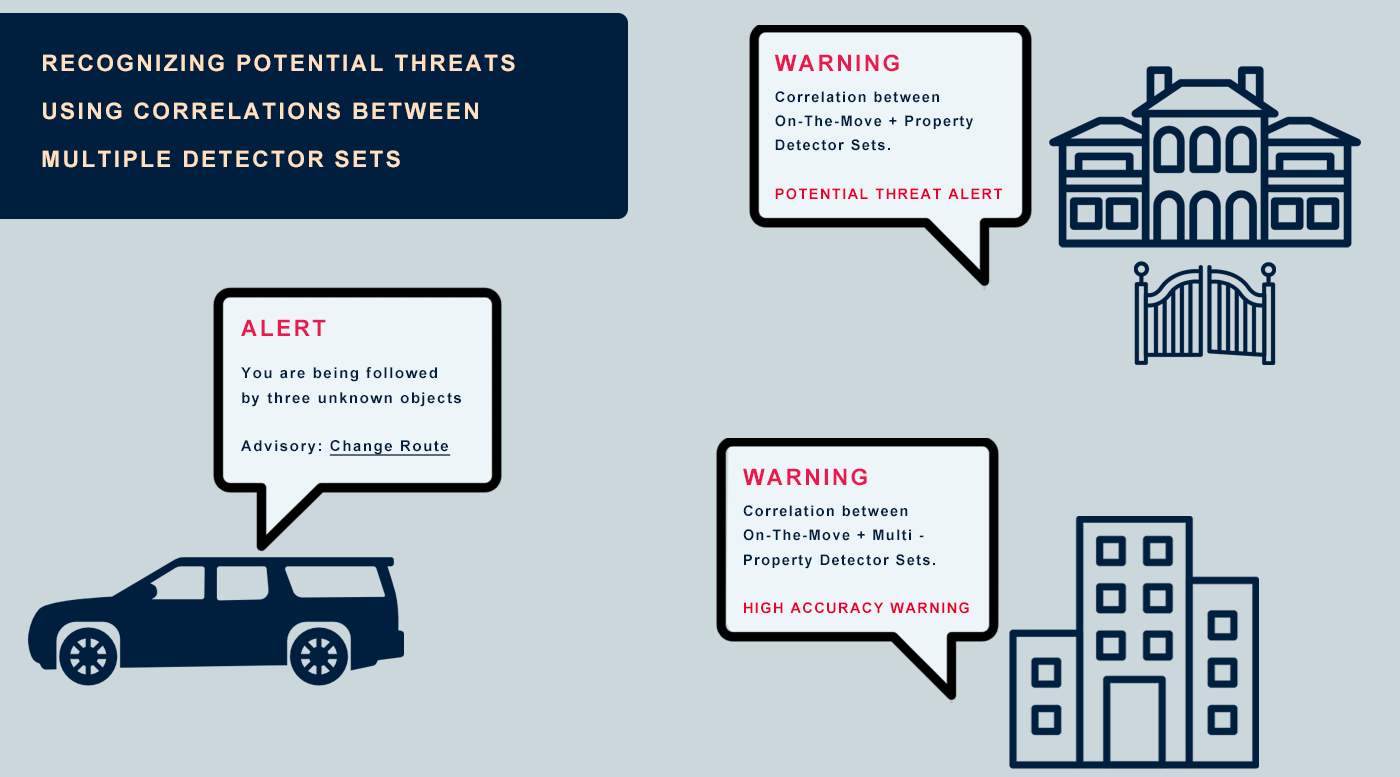
The System immediately alerts you, your team or the control room when it recognizes object detection correlations between different X•Protected Sets. Several preset scenarios are available and you have the option to personalize scenarios.
The System deciphers invisible patterns into visible patterns. At the same time, these patterns are processed, correlated and translated into valuable intelligence.
This makes it possible to identify 1st and 2nd layer connections, so that any suspicious activity can be recognized even faster. In the (explanatory) animation below, you can see how the system makes connections between unknown and previously detected objects.
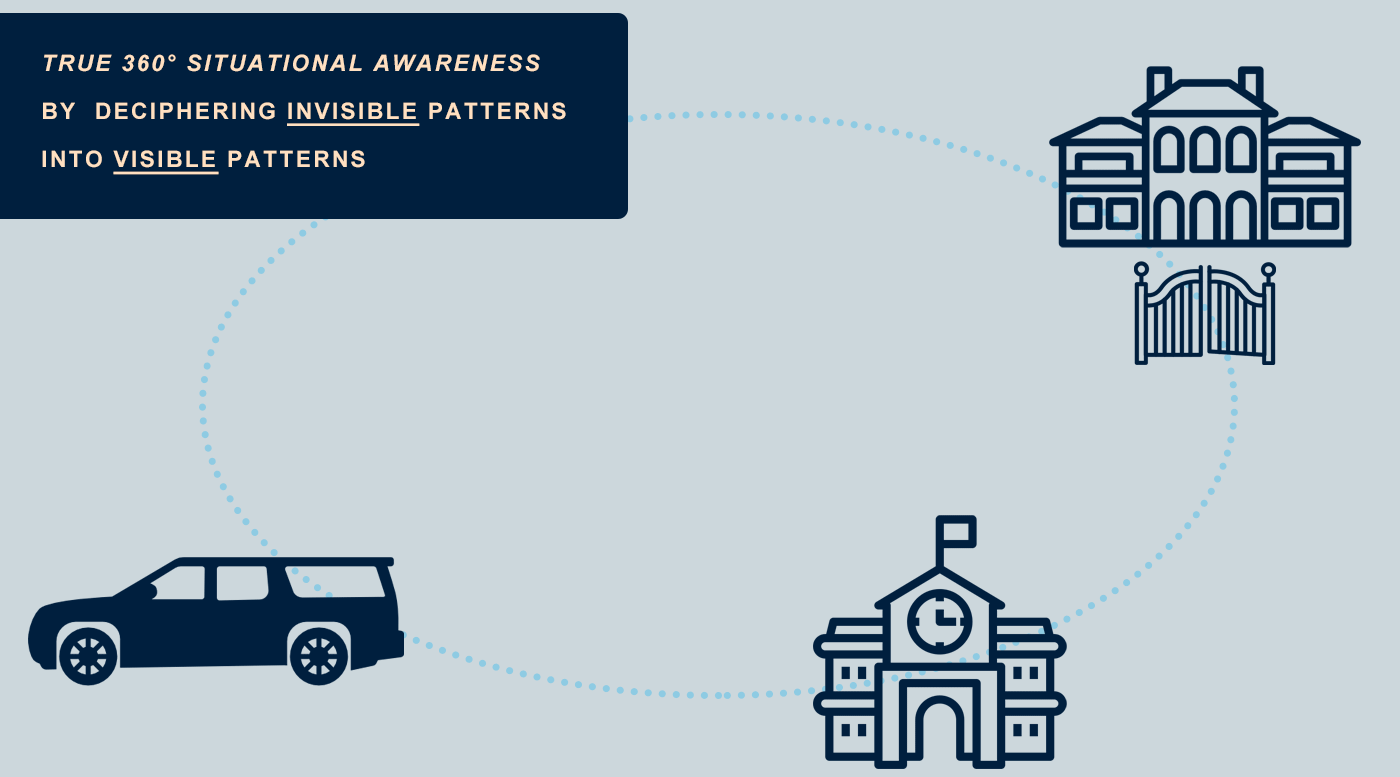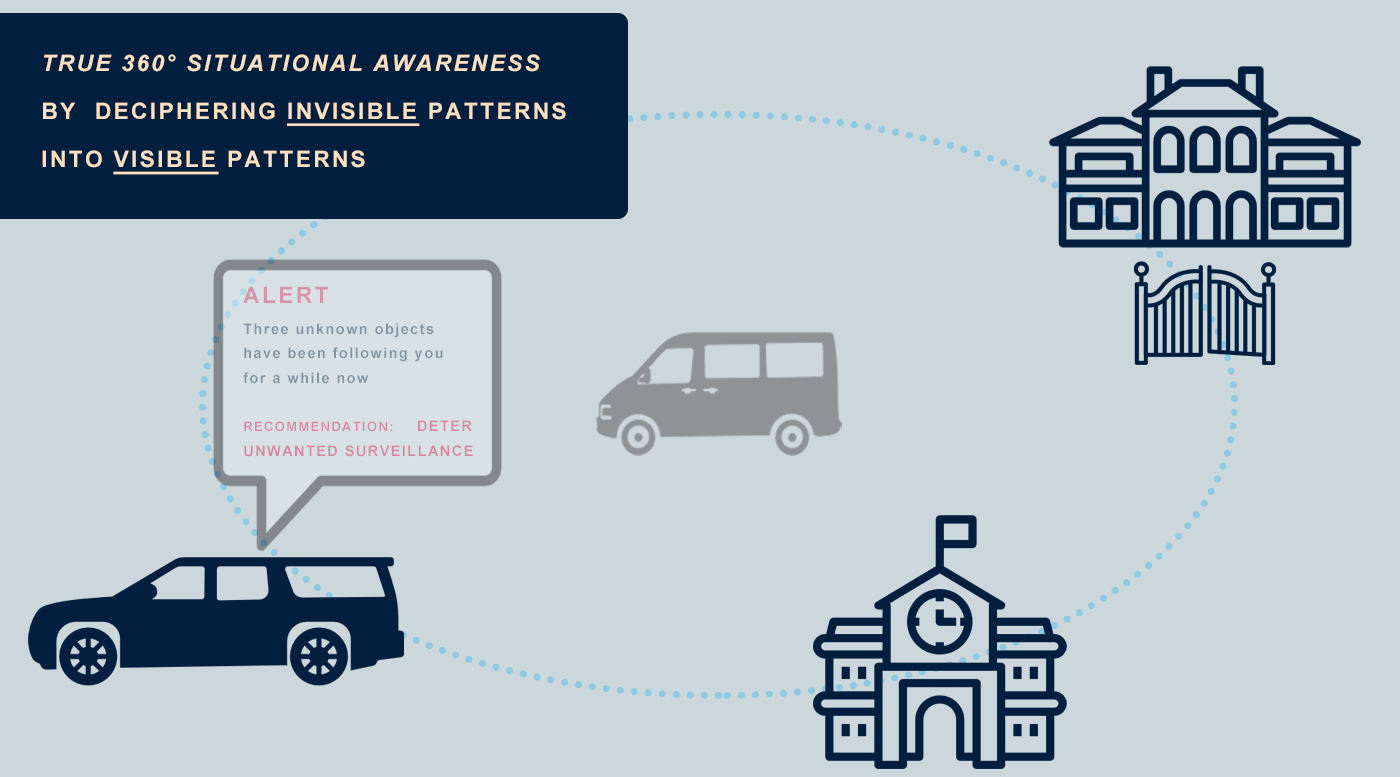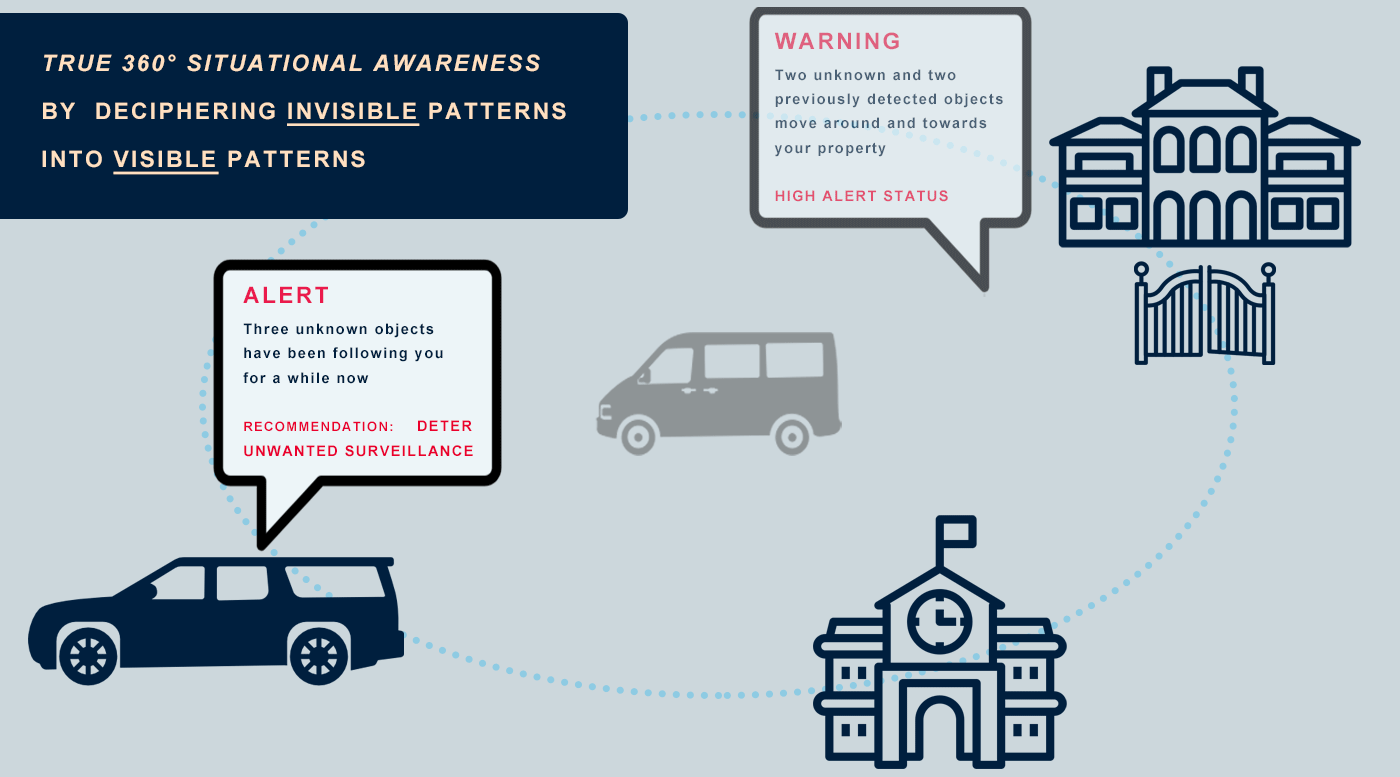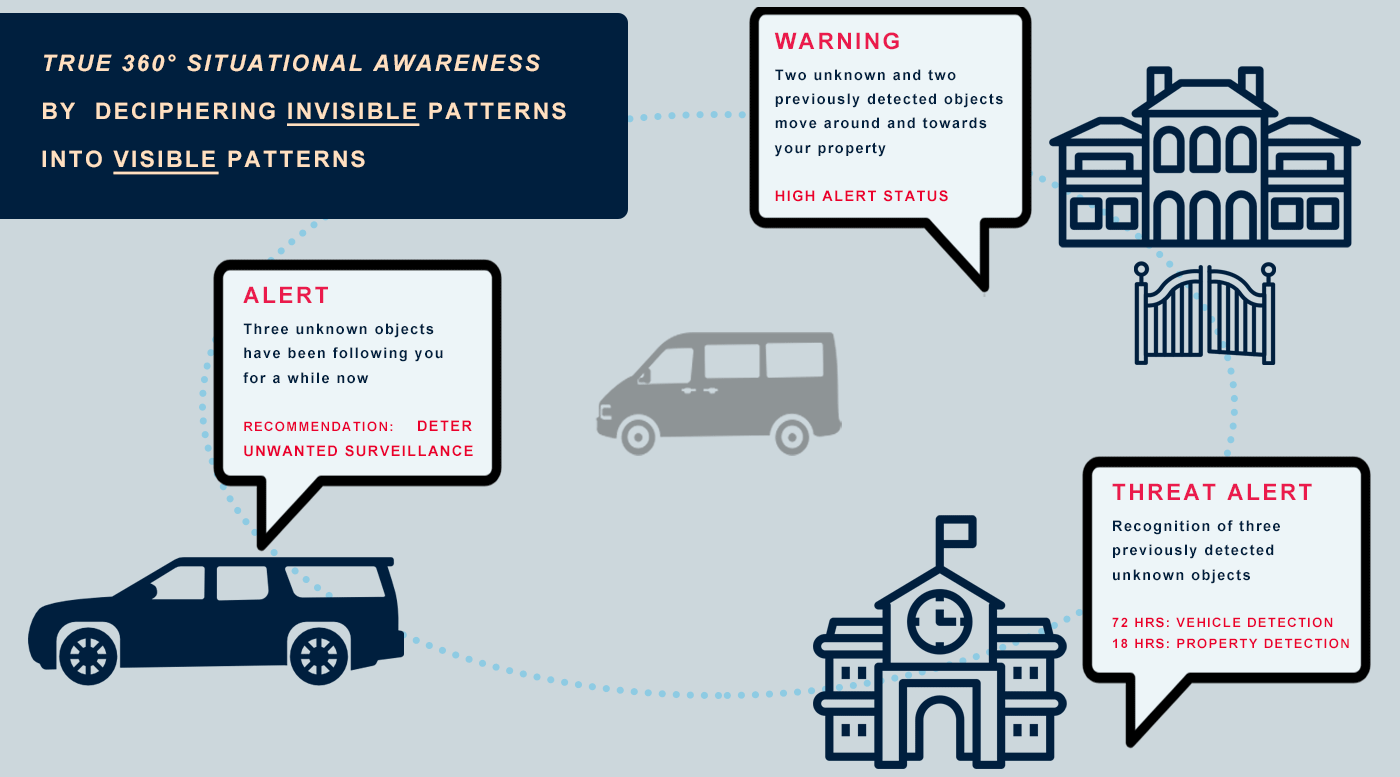
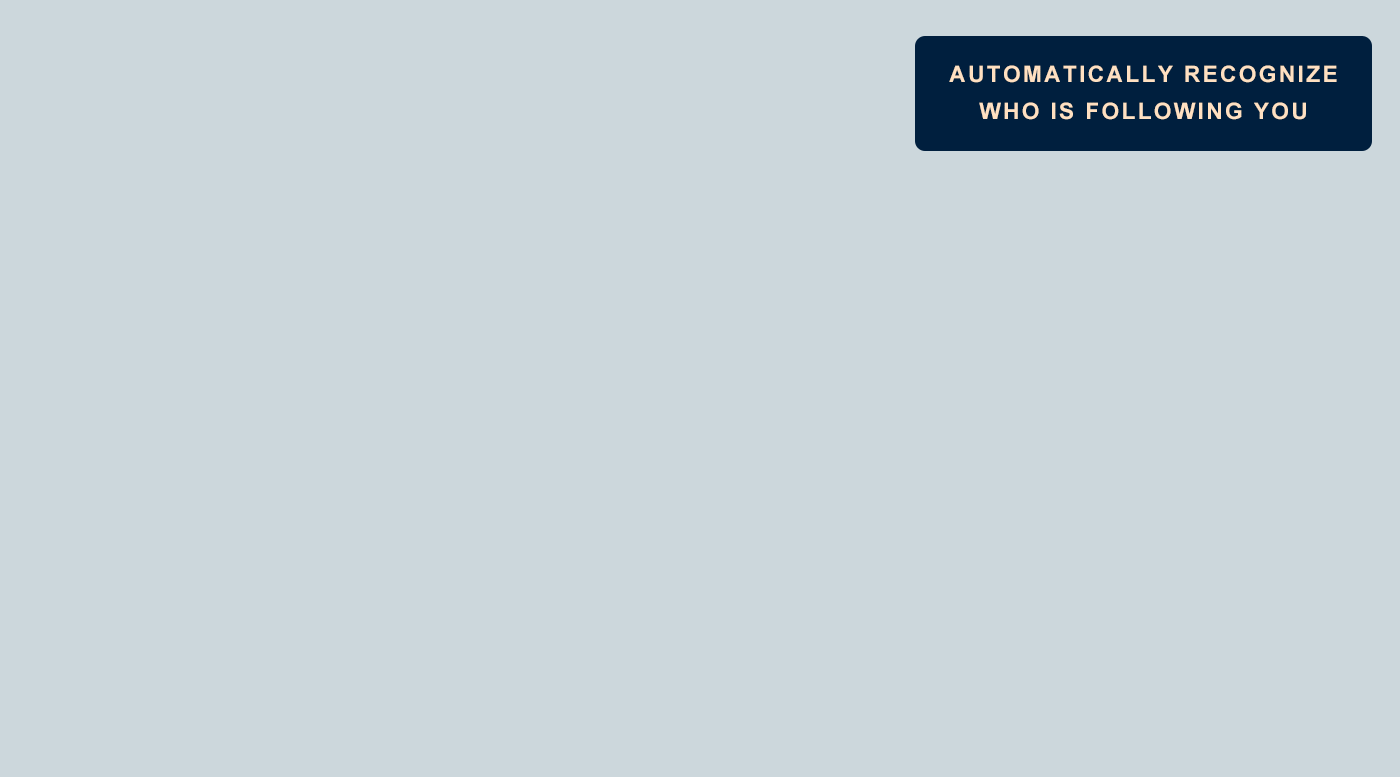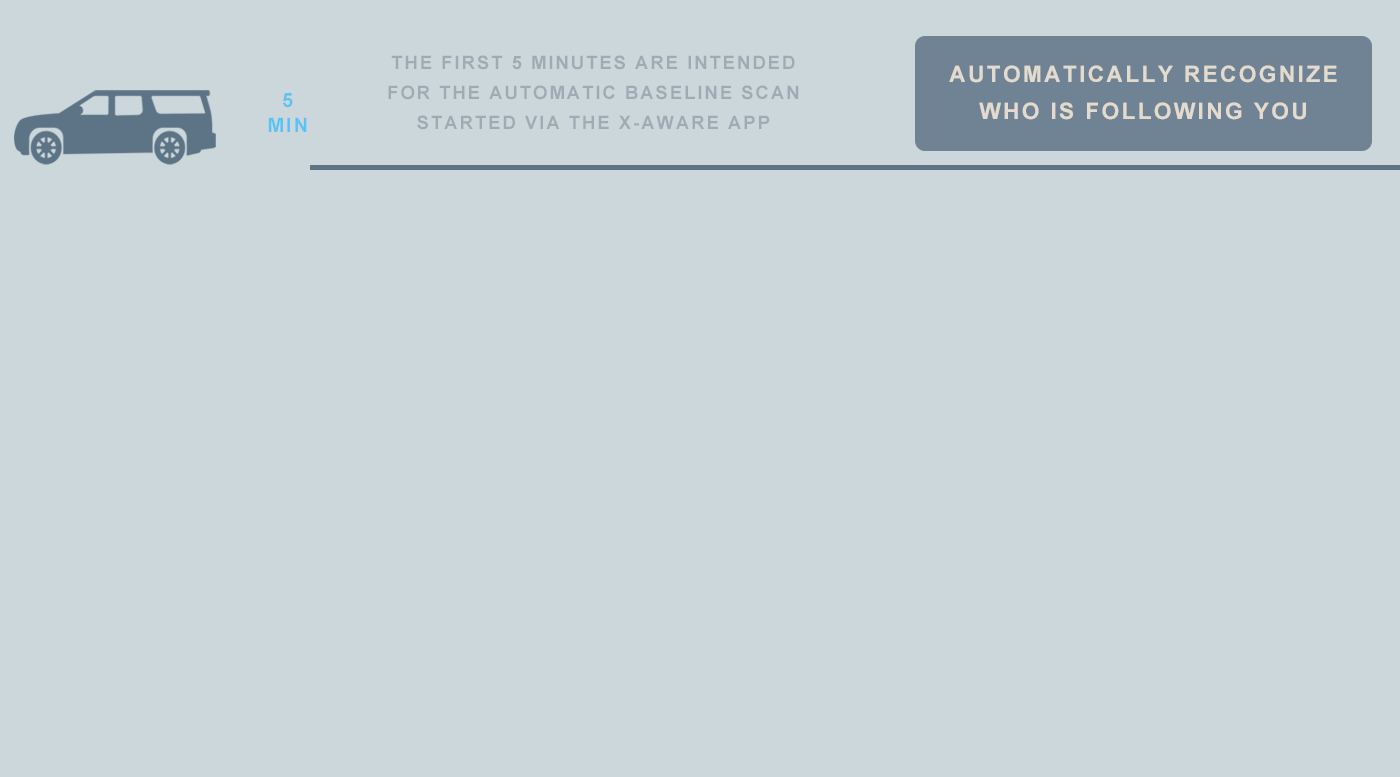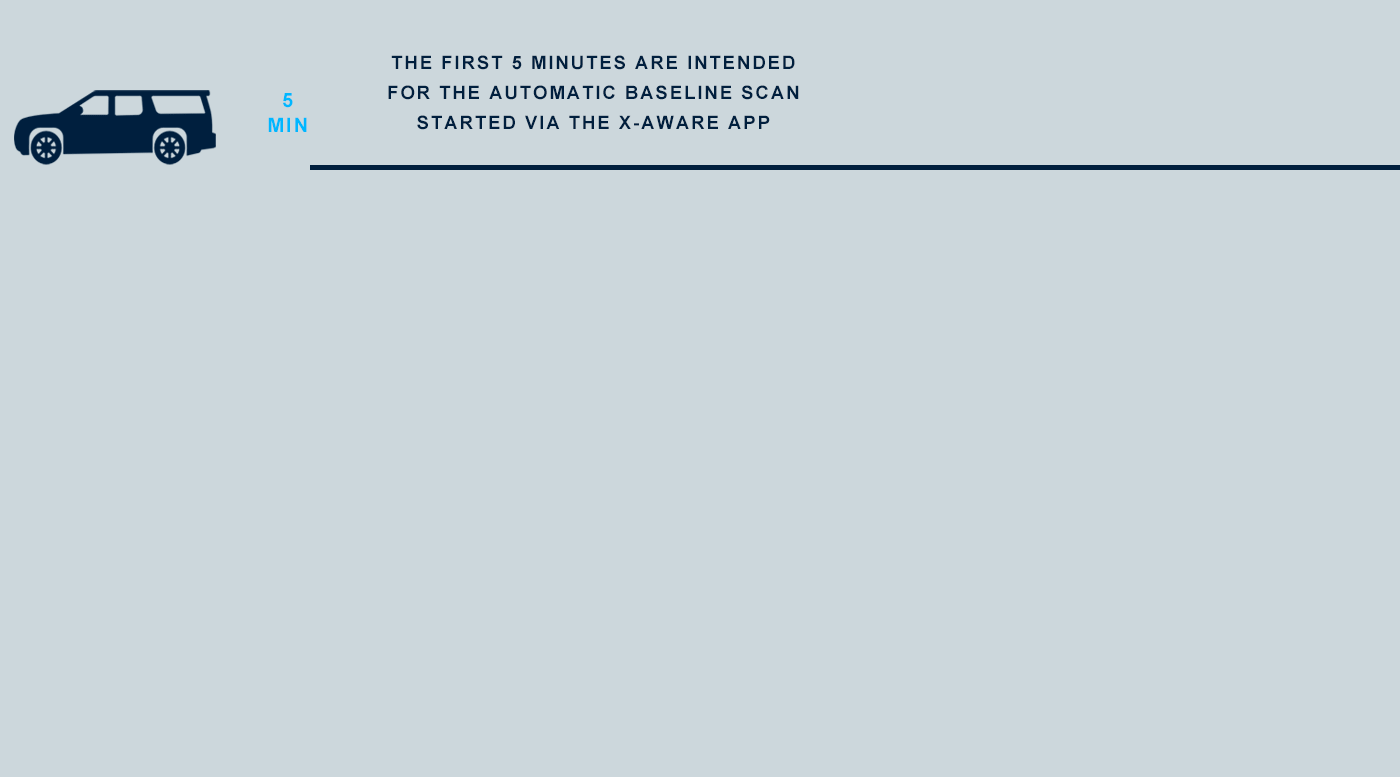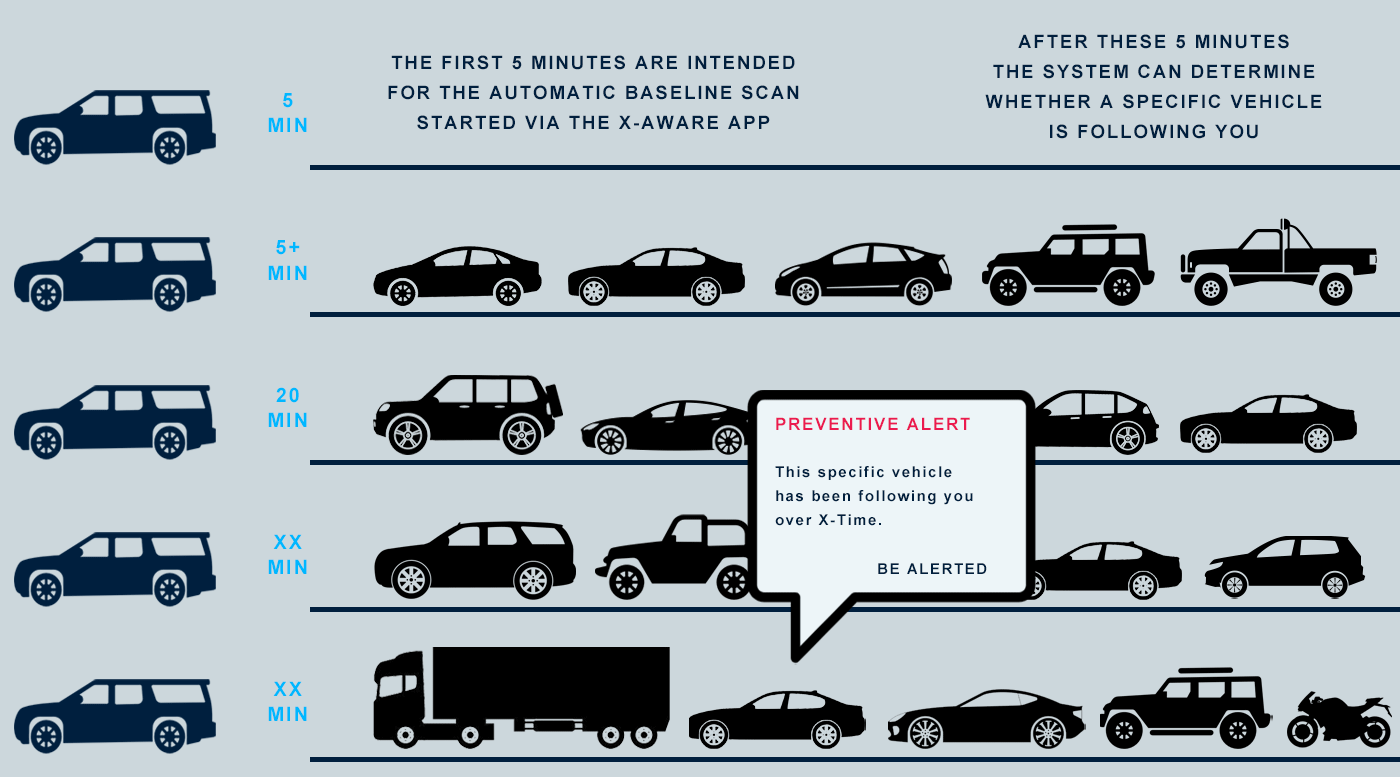
The system recognizes when you are being unknowingly watched, even when you are travelling. There is no need to enter data manually, the system adapts in real time based on the information collected based on Adaptive Learning.
The (explanatory) animation below explains various use cases, which can also be combined.
